
Overview
This articles intends to document how to configure SSO for each protocol available to WebShare Enterprise.
Protocols covered in this document:
- SSO with LDAP
- SSO with Microsoft Azure Active Directory
- SSO with OpenID Connect
- SSO with SAML 2.0
- Custom DEX Connector
|
Parameters:
- LDAPS root CA
- Only necessary if using secure LDAP – LDAPS.
- LDAP bind DN (required)
- DN bind configured within the LDAP – ie: cn=admin,dc=example,dc=org.
- LDAP bind password (required)
- The password for the bind configured withing the LDAP.
- LDAP user base DN (required)
- The starting point an LDAP server uses when searching for users authentication within your Directory – ie: ou=People.
|

Example configuration of SSO with LDAP |
|
Parameters:
- Redirect URI
- Redirect URI to be configured in the Microsoft Azure Active Directory side, should look like “https://<your-domain/dex/callback”.
- Directory tenant ID (required)
- The ID of the directory tenant ID configured in Azure.
- Application client ID (required)
- The ID of the application created in Azure.
- Client secret (required)
- Secret created for the application created in Azure.
- Allowed Groups (optional)
- Alias of the groups within the Active Directory.
|

Example configuration of SSO with Microsoft Azure Active Directory |
|
Parameters:
- Redirect URI
- Redirect URI to be configured in the OpenID issuer, should look like “https://<your-domain/dex/callback”.
- Issuer URI (required)
- The URL of the OpenID issuer portal.
- Client ID (required)
- Client ID configured within the OpenID issuer.
- Client secret (required)
- The secret configured for the Client ID configured within the OpenID issuer.
|

Example configuration for SSO with OpenID Connect |
|
Parameters:
- Redirect URI
- Redirect URI to be configured in the Microsoft Azure Active Directory side, should look like “https://<your-domain/dex/callback”.
- SAML Entity Issuer URL (required)
- The entity Issuer of WSE, should look like “https://<your-domain/dex/”.
- Identity provider login URL (required)
- The URL of the identity provider login page
- Identity provider certificate (optional - recommended)
- Certificate body – full chain
- SAML NameID format
- Options available:
- Persistent
- emailAddress
- unspecified
- X509SubjectName
- WindowsDomainQualifiedName
- Encrypted
- Entity
- Kerberos
- Transient
- Configure the one that applies for the identity provider.
- Username attribute
- The attribute of the user name configured in the identity provider – ie: User ID
- Email address attribute
- The attribute of the email address configured in the identity provider
- Group attribute (optional)
- Group delimiter
- Only needed when all groups are returned by the SAML 2.0 server as a single string.
- Allowed groups
- Optionally specify one or more comma-separated groups to restrict access to WebShare Enterprise. Only users that are restricted access to WebShare Enterprise.
- Only users that are a member of at least one of those groups will be allowed to log in.
|

Example configuration for SSO with SAML 2.0 |
|
Parameters:
- Redirect URI
- Redirect URI to be configured in the Microsoft Azure Active Directory side, should look like “https://<your-domain/dex/callback”.
- Text box to fill the custom DEX configuration
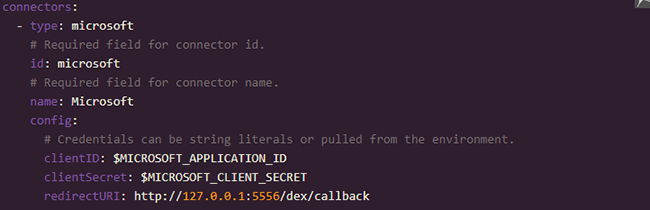
Custom Dex Connector - Microsoft
|

Example configuration of SSO with Custom DEX Connector
|







